Stats and Conclusions for Windows Server 2016
In this article we present statistics and conclusions about privacy implications of Windows Server 2016. This report is based on traffic recording of virtual machine running Windows Server 2016, which was run continuously for 505 days, from 2018-02-03 to 2019-07-20. After the installation, Windows Server 2016 was switched to zero (Security) level of telemetry via Group Policy Editor (gpedit.msc). Then OS was left alone. It had default settings and was running without any third party software installed. In total, we have recorded and analyzed 39,921,165,760 bytes of received and transmitted data.
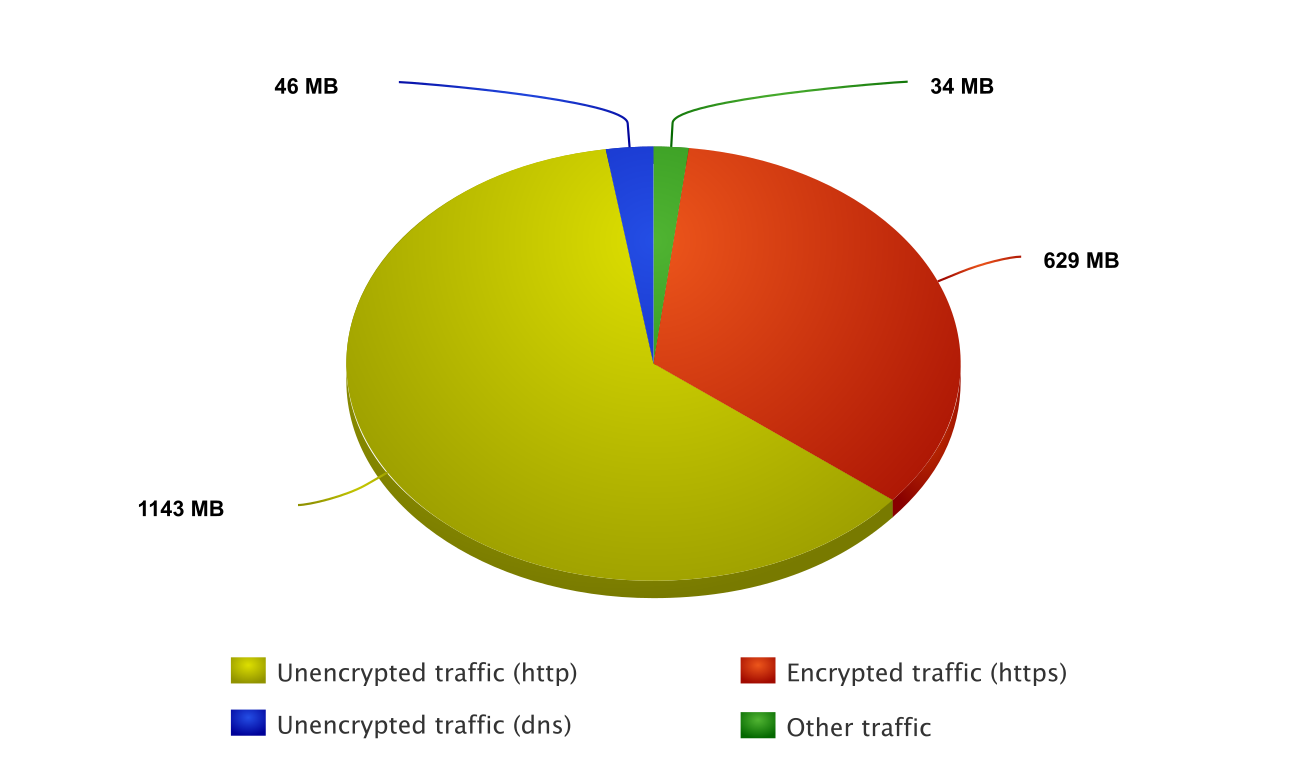
Outgoing traffic
| Bytes transmitted | Ratio | Traffic type | ||
|---|---|---|---|---|
| 1,198,884,996 | 61.73% | Unencrypted traffic (http) | ||
| 659,067,954 | 33.93% | Encrypted traffic (https) | ||
| 48,544,205 | 2.50% | Unencrypted traffic (dns) | ||
| 35,806,172 | 1.84% | Other traffic (dhcp, icmp, LAN broadcasts) | ||
| 1,942,303,327 | 100% | Total |
Incoming traffic
| Bytes received | Ratio | Traffic type | ||
|---|---|---|---|---|
| 36,428,643,464 | 97.91% | Unencrypted traffic (http) | ||
| 732,594,839 | 1.97% | Encrypted traffic (https) | ||
| 39,525,093 | 0.11% | Unencrypted traffic (dns) | ||
| 5,645,192 | 0.01% | Other traffic (dhcp, icmp, LAN broadcasts) | ||
| 37,206,408,588 | 100% | Total |
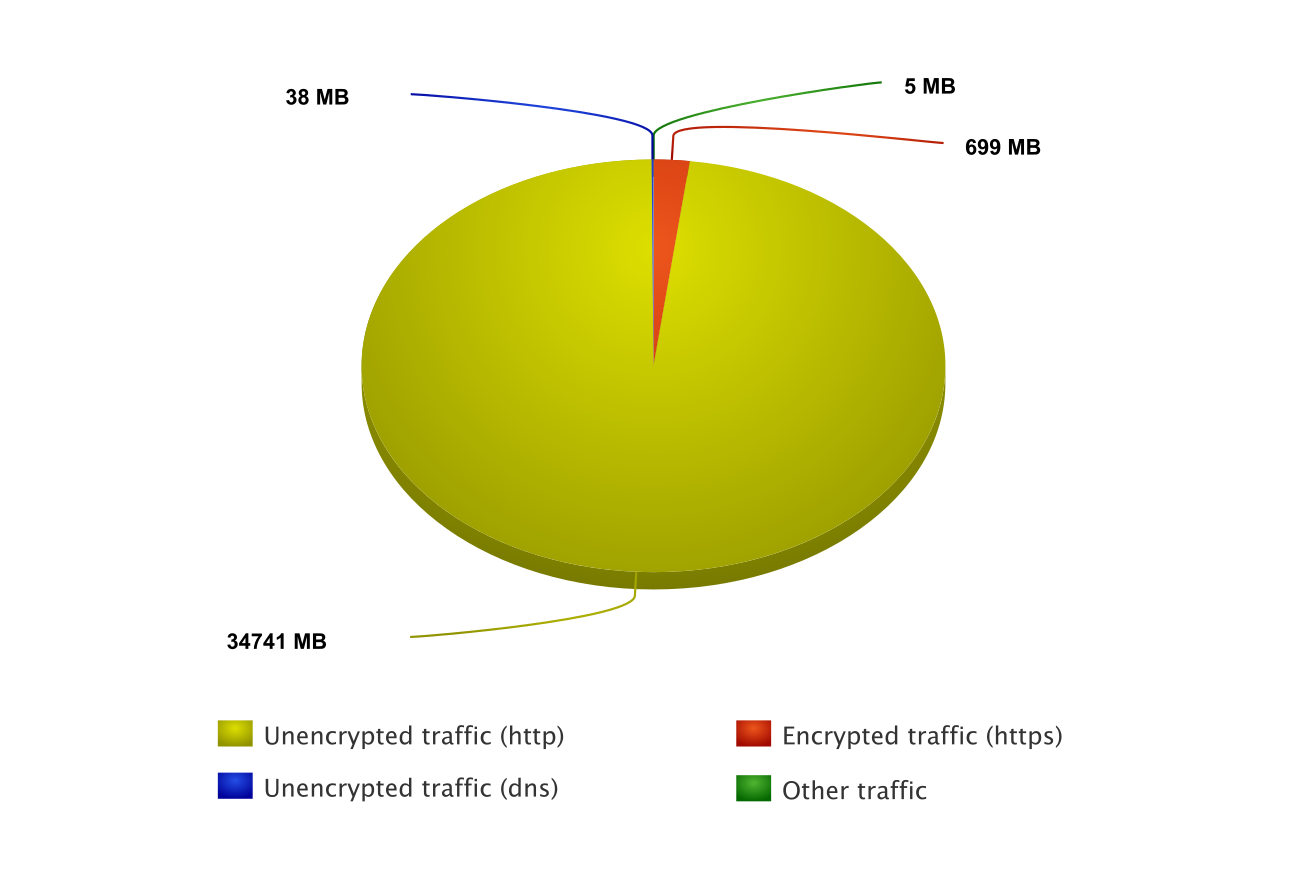
Conclusion: most part of incoming data (such as updated Windows binary files) is not encrypted. This is probably to reduce the load on Microsoft cloud infrastructure.
IP addresses
Outgoing HTTPS connections
… | Outgoing HTTP connections
… |
Conclusion: blacklisting of so many IP addresses on the firewall seems impractical. They belong to many different subnets all over the globe, and probably some of them depend on geographical location or identity of the end user.
Domain names
Outgoing HTTPS connections
… | Outgoing HTTP connections
… |
Conclusion: Unlike Windows 10, for Windows Server 2016 telemetry traffic blocking is practical on the DNS level, at least while level of telemetry is set to zero (Security). This requires some generalization (wildcard domain names in blocking rules), as domain names may vary depending on geographical location or identity of the end user, current time, Windows Server build number, etc.
Autonomous systems
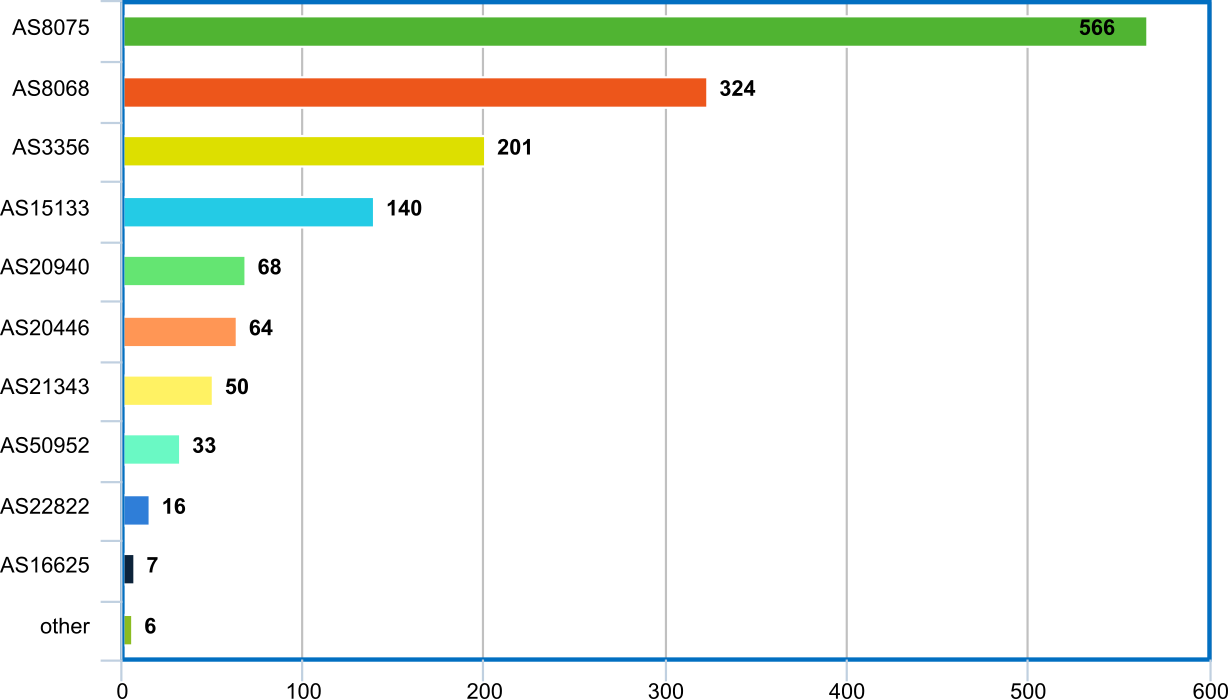
Outgoing traffic breakdown by AS
Bytes transmitted | Ratio | AS Number | Organization | |||
|---|---|---|---|---|---|---|
| 593,822,751 | 38.43% | AS8075 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 339,797,523 | 21.99% | AS8068 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 210,290,726 | 13.61% | AS3356 | LEVEL3 – Level 3 Communications, Inc., US | |||
| 146,731,160 | 9.50% | AS15133 | EDGECAST – MCI Communications Services, Inc. d/b/a Verizon Business, US | |||
| 71,170,466 | 4.61% | AS20940 | AKAMAI-ASN1, US | |||
| 66,945,670 | 4.33% | AS20446 | HIGHWINDS3 – Highwinds Network Group, Inc., US | |||
| 52,340,110 | 3.39% | AS21343 | ALLIED – Allied Standart Limited LLC, UA | |||
| 34,425,103 | 2.23% | AS50952 | DATAIX-AS – Peering Ltd., RU | |||
| 16,639,254 | 1.08% | AS22822 | LLNW – Limelight Networks, Inc., US | |||
| 7,157,259 | 0.46% | AS16625 | AKAMAI-AS – Akamai Technologies, Inc., US | |||
| 5,829,418 | 0.38% | other |
Incoming traffic breakdown by AS
Bytes received | Ratio | AS Number | Organization | |||
|---|---|---|---|---|---|---|
| 10,934,939,834 | 30.88% | AS8068 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 8,314,353,265 | 23.48% | AS3356 | LEVEL3 – Level 3 Communications, Inc., US | |||
| 5,896,117,091 | 16.65% | AS15133 | EDGECAST – MCI Communications Services, Inc. d/b/a Verizon Business, US | |||
| 3,124,783,119 | 8.83% | AS20940 | AKAMAI-ASN1, US | |||
| 2,202,774,948 | 6.22% | AS21343 | ALLIED – Allied Standart Limited LLC, UA | |||
| 2,186,811,262 | 6.18% | AS20446 | HIGHWINDS3 – Highwinds Network Group, Inc., US | |||
| 1,618,390,659 | 4.57% | AS50952 | DATAIX-AS – Peering Ltd., RU | |||
| 600,642,763 | 1.70% | AS8075 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 333,859,670 | 0.94% | AS22822 | LLNW – Limelight Networks, Inc., US | |||
| 148,296,651 | 0.42% | AS1299 | TELIANET – Telia Carrier, SE | |||
| 47,124,951 | 0.13% | other |
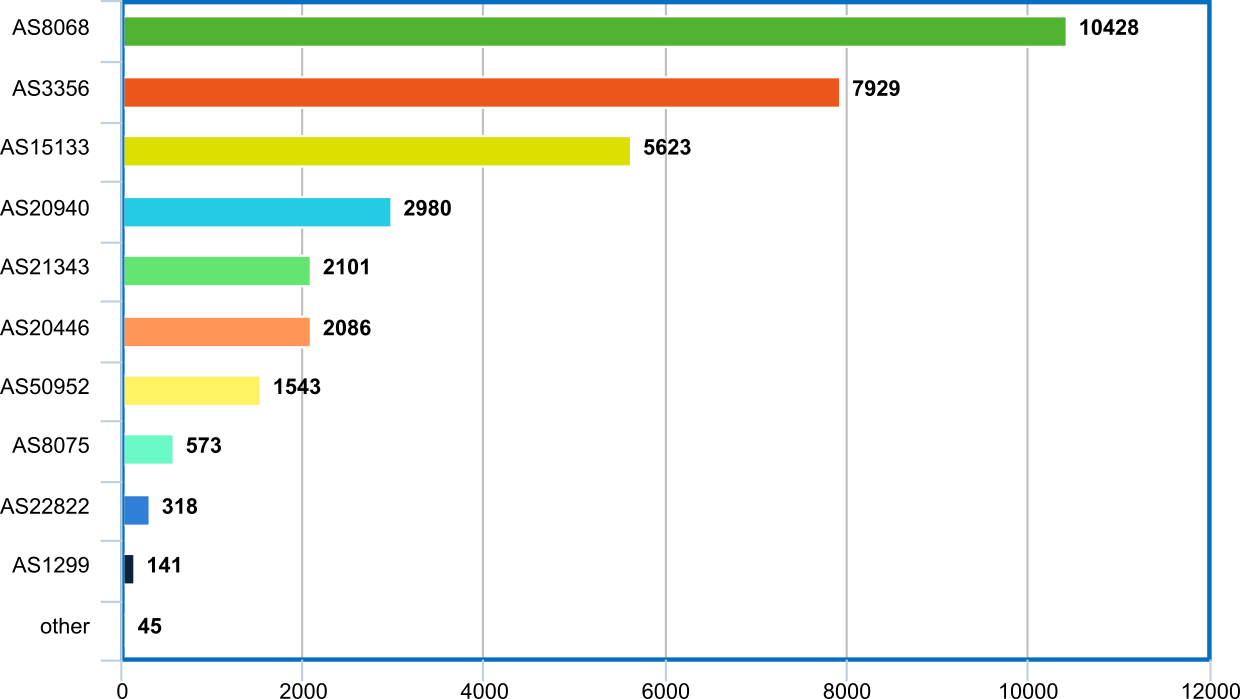
Conclusion: two Microsoft autonomous systems clearly dominate, but there are others as well. Autonomous systems of AKAMAI, LEVEL3 and other cloud providers can’t be blocked on the firewall level, because normal operation of too many systems will be broken — stable connectivity to these servers is required not only by Microsoft’s products.