Privacy Implications of Windows 10 Telemetry: Summary Stats and Conclusions
In this article we present summary statistics and conclusions about privacy implications of Windows 10. This report is based on traffic recording of virtual machine with Windows 10, which was run continuously for 346 days, from 2017-02-15 to 2018-01-27. After the installation, Windows 10 was left alone. This OS had default settings and was running without any third party software installed. In total, we have recorded and analyzed 55,945,178,210 bytes of received and transmitted data.
Previous articles:
- About Windows 10 telemetry experiment
- Virtual machine network setup
- Configuration of traffic recording software
- Processing of raw traffic dumps
Outgoing traffic
| Bytes transmitted | Ratio | Traffic type | ||
|---|---|---|---|---|
| 2,741,192,873 | 59.68% | Encrypted traffic (https) | ||
| 1,783,520,334 | 38.83% | Unencrypted traffic (http) | ||
| 50,795,566 | 1.11% | Unencrypted traffic (dns) | ||
| 17,666,863 | 0.38% | Other traffic (dhcp, icmp, LAN broadcasts) | ||
| 4,593,175,636 | 100% | Total |
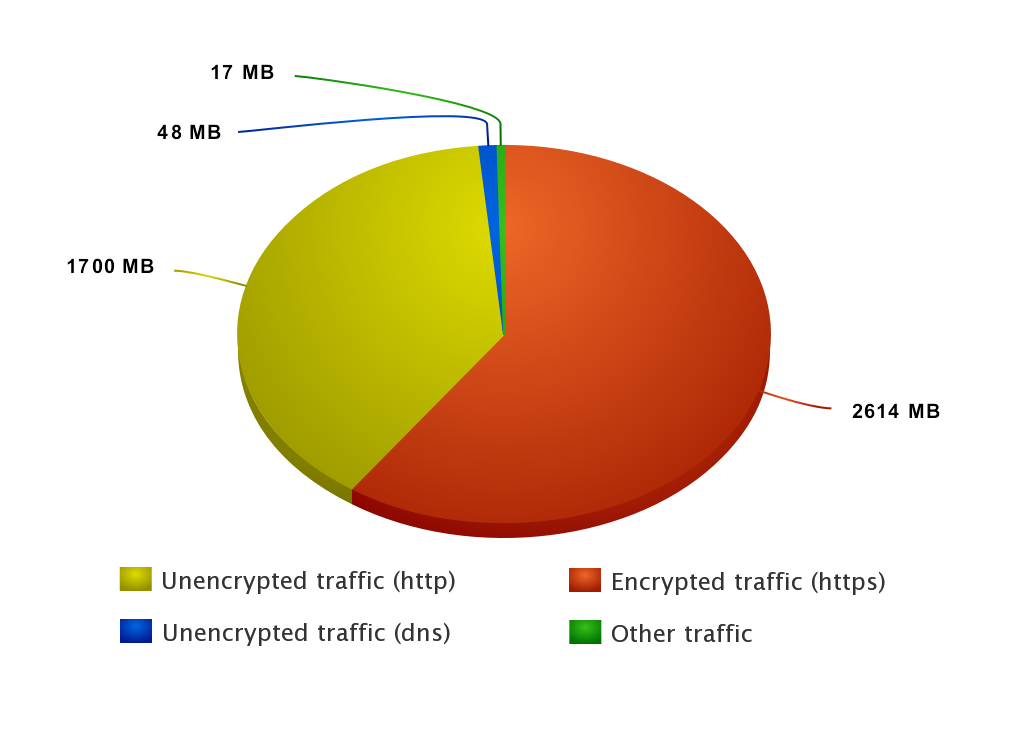
Conclusion: most part of outgoing telemetry data is encrypted in such way that it can’t be decrypted by end user or ISP, only by Microsoft and third parties trusted by Microsoft.
Incoming traffic
| Bytes received | Ratio | Traffic type | ||
|---|---|---|---|---|
| 43,157,429,704 | 84.04% | Unencrypted traffic (http) | ||
| 8,127,912,364 | 15.83% | Encrypted traffic (https) | ||
| 61,606,053 | 0.12% | Unencrypted traffic (dns) | ||
| 4,994,930 | 0.01% | Other traffic (dhcp, icmp, LAN broadcasts) | ||
| 51,351,943,051 | 100% | Total |
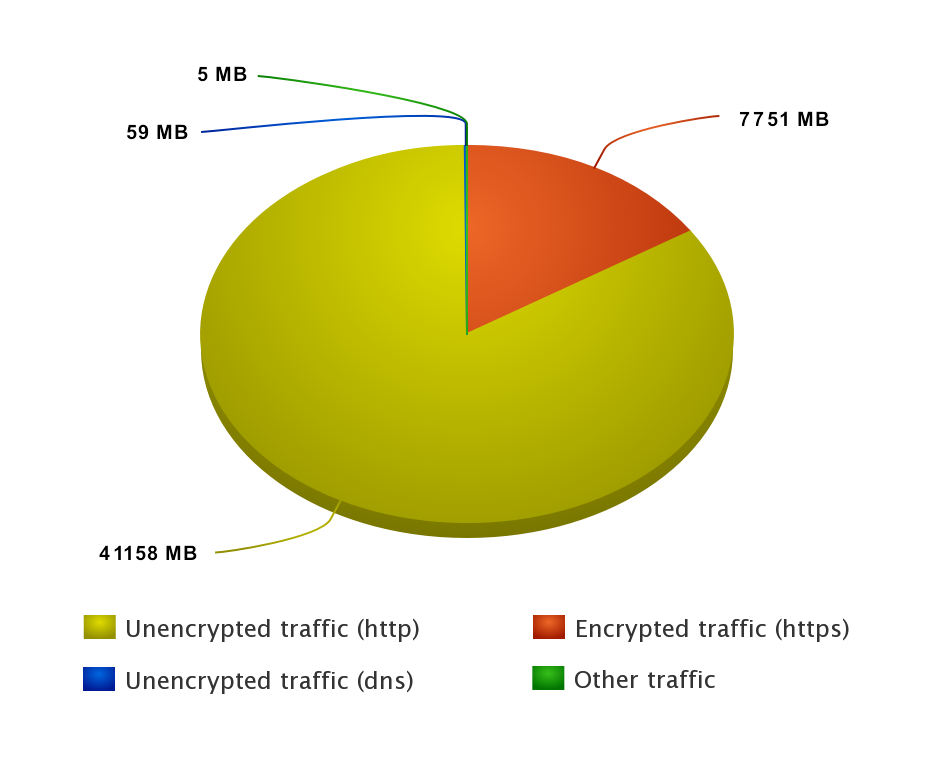
Conclusion: most part of incoming data (such as updated Windows binary files) is not encrypted. This is probably to reduce the load on Microsoft cloud infrastructure.
IP addresses
Outgoing HTTPS connections
| Number of connections | IP address | |
|---|---|---|
| 140795 | 191.239.213.227 | |
| 44591 | 40.77.226.250 | |
| 41686 | 204.79.197.200 | |
| 34451 | 13.107.21.200 | |
| 34130 | 138.91.119.16 | |
| 31434 | 204.79.197.213 | |
| 30433 | 40.77.226.246 | |
| 30153 | 40.77.226.247 | |
| 26371 | 2.17.158.154 | |
| 26241 | 40.77.226.249 | |
| 23845 | 104.81.62.81 | |
| 10565 | 23.59.117.40 | |
| 8539 | 52.178.178.16 | |
| 8524 | 23.59.98.213 | |
| 8223 | 40.113.87.220 | |
| 7490 | 23.64.226.172 | |
| 7000 | 23.59.97.117 | |
| 6010 | 13.107.3.128 | |
| 5967 | 131.253.61.82 | |
| 5456 | 40.77.228.74 | |
| 5391 | 131.253.61.64 | |
| 5081 | 131.253.61.80 | |
| 5023 | 184.31.86.169 | |
| 4915 | 131.253.61.96 | |
| 4752 | 131.253.61.68 |
. . .
Outgoing HTTP connections
| Number of connections | IP address | |
|---|---|---|
| 14475 | 13.107.4.50 | |
| 12487 | 2.17.158.154 | |
| 6474 | 2.17.157.178 | |
| 4857 | 2.17.157.233 | |
| 4839 | 151.101.1.108 | |
| 4496 | 23.59.97.117 | |
| 4310 | 104.96.131.83 | |
| 3707 | 23.64.226.172 | |
| 3158 | 104.85.245.204 | |
| 2879 | 104.81.240.210 | |
| 2775 | 2.20.254.115 | |
| 2434 | 13.107.4.52 | |
| 2226 | 23.59.89.164 | |
| 2169 | 2.20.254.99 | |
| 2159 | 134.170.111.154 | |
| 2159 | 134.170.104.154 | |
| 2108 | 172.227.139.113 | |
| 1902 | 80.239.244.148 | |
| 1871 | 23.64.229.220 | |
| 1844 | 23.45.239.243 | |
| 1715 | 213.248.116.179 | |
| 1643 | 23.64.225.126 | |
| 1402 | 37.252.172.40 | |
| 1402 | 2.17.212.200 | |
| 1316 | 207.46.194.14 |
. . .
Conclusion: blacklisting of so many IP addresses on the firewall seems impractical. They belong to many different subnets all over the globe, and probably some of them depend on geographical location or identity of the end user.
Domain names
Outgoing HTTPS connections
| Number of connections | Domain name | |
|---|---|---|
| 174925 | personalization.services.msn.com. | |
| 62340 | cdn.content.prod.cms.msn.com. | |
| 46253 | login.live.com. | |
| 44258 | v10.vortex-win.data.microsoft.com. | |
| 39767 | client.wns.windows.com. | |
| 35119 | settings-win.data.microsoft.com. | |
| 31019 | www.bing.com. | |
| 28954 | adbroker.mp.dse.microsoft.com. | |
| 27320 | g.bing.com. | |
| 21146 | skydrive.wns.windows.com. | |
| 19824 | cdn.onenote.net. | |
| 16987 | ieonline.microsoft.com. | |
| 16317 | api.onedrive.com. | |
| 13301 | skyapi.live.net. | |
| 12764 | t0.ssl.ak.dynamic.tiles.virtualearth.net. | |
| 12067 | by3302.storage.live.com. | |
| 11618 | t0.ssl.ak.tiles.virtualearth.net. | |
| 11135 | mobile.pipe.aria.microsoft.com. | |
| 8784 | c.urs.microsoft.com. | |
| 5997 | fe2.update.microsoft.com. | |
| 5426 | ecn.dev.virtualearth.net. | |
| 5426 | bn2ap002.device.ra.live.com. | |
| 4920 | ssw.live.com. | |
| 3704 | pipe.skype.com. | |
| 3671 | am3pap001.storage.live.com. |
. . .
Outgoing HTTP connections
| Number of connections | Domain name | |
|---|---|---|
| 39704 | cdn.content.prod.cms.msn.com. | |
| 22043 | cdn.appex-rf.msn.com. | |
| 18778 | tile-service.weather.microsoft.com. | |
| 7594 | ams1-ib.adnxs.com. | |
| 7210 | ib.adnxs.com. | |
| 7106 | tlu.dl.delivery.mp.microsoft.com. | |
| 6871 | au.download.windowsupdate.com. | |
| 6614 | ssw.live.com. | |
| 5905 | fra1-ib.adnxs.com. | |
| 5653 | vcdn.adnxs.com. | |
| 4632 | 7.tlu.dl.delivery.mp.microsoft.com. | |
| 4135 | au.b1.download.windowsupdate.com. | |
| 2518 | ctldl.windowsupdate.com. | |
| 2434 | www.msftconnecttest.com. | |
| 2351 | 2.tlu.dl.delivery.mp.microsoft.com. | |
| 2220 | download.windowsupdate.com. | |
| 2064 | secure.adnxs.com. | |
| 1282 | img-s-msn-com.akamaized.net. | |
| 1086 | cdn.adnxs.com. | |
| 1011 | go.microsoft.com. | |
| 917 | ocsp.digicert.com. | |
| 857 | 7.dl.delivery.mp.microsoft.com. | |
| 719 | ocsp.msocsp.com. | |
| 696 | 3.tlu.dl.delivery.mp.microsoft.com. | |
| 671 | g.live.com. |
. . .
Conclusion: Windows 10 telemetry is heavily intertwined with other Microsoft products and services, such as Bing, Skype, OneDrive, OneNote, Office 365, Live.com and MSN. Blacklisting of so many services on the firewall seems impractical. Some of these domain names contain numeric components which may change frequently, or may depend on geographical location or identity of the end user.
Autonomous systems
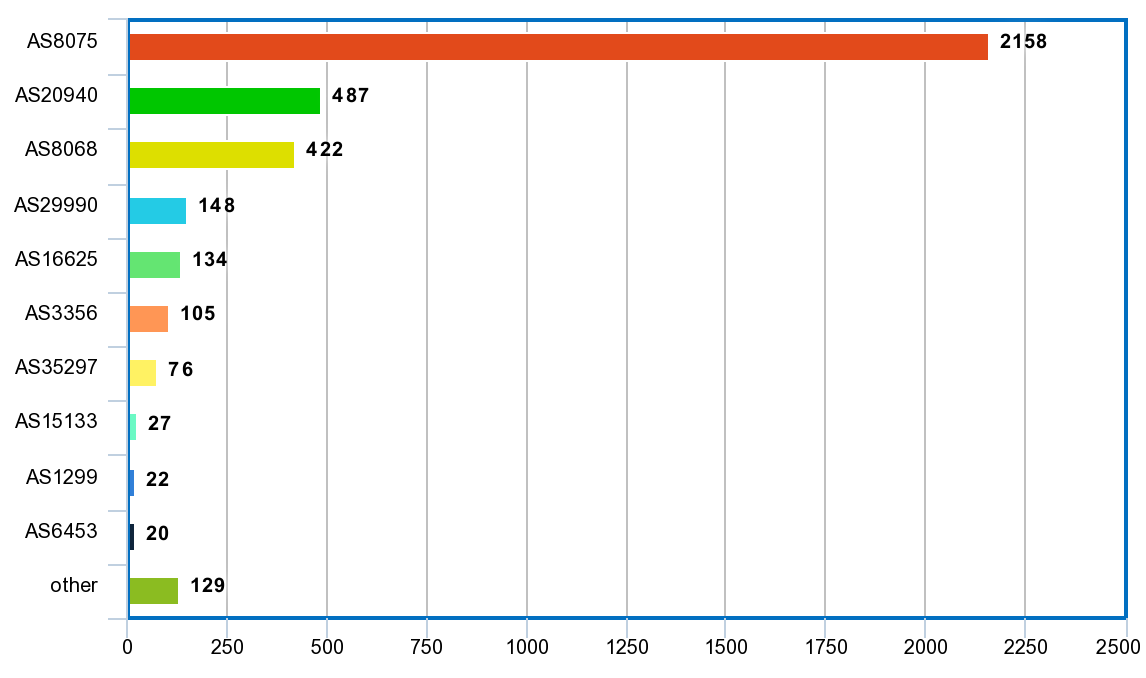
Outgoing traffic breakdown by AS
| Bytes transmitted | Ratio | AS Number | Organization | |||
|---|---|---|---|---|---|---|
| 2,262,395,574 | 57.87% | AS8075 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 510,651,915 | 13.06% | AS20940 | AKAMAI-ASN1, US | |||
| 442,009,608 | 11.31% | AS8068 | MICROSOFT-CORP-MSN-AS-BLOCK – Microsoft Corporation, US | |||
| 155,343,693 | 3.97% | AS29990 | ASN-APPNEXUS – AppNexus, Inc, US | |||
| 140,783,568 | 3.60% | AS16625 | AKAMAI-AS – Akamai Technologies, Inc., US | |||
| 110,246,261 | 2.82% | AS3356 | LEVEL3 – Level 3 Communications, Inc., US | |||
| 79,388,801 | 2.03% | AS35297 | DATALINE-AS, UA | |||
| 28,791,644 | 0.74% | AS15133 | EDGECAST – MCI Communications Services, Inc. d/b/a Verizon Business, US | |||
| 23,428,535 | 0.60% | AS1299 | TELIANET Telia Carrier, SE | |||
| 21,281,019 | 0.54% | AS6453 | TATA COMMUNICATIONS (AMERICA) INC, US | |||
| 135,457,590 | 3.46% | other |
Incoming traffic breakdown by AS
| Bytes received | Ratio | AS Number | Organization | |||
|---|---|---|---|---|---|---|
| 17,349,724,492 | 37.54% | AS8068 | MICROSOFT-CORP-MSN-AS-BLOCK - Microsoft Corporation, US | |||
| 12,879,649,485 | 27.87% | AS20940 | AKAMAI-ASN1, US | |||
| 4,126,384,740 | 8.93% | AS8075 | MICROSOFT-CORP-MSN-AS-BLOCK - Microsoft Corporation, US | |||
| 3,606,725,593 | 7.80% | AS3356 | LEVEL3 - Level 3 Communications, Inc., US | |||
| 2,482,047,760 | 5.37% | AS35297 | DATALINE-AS, UA | |||
| 1,071,251,663 | 2.32% | AS16625 | AKAMAI-AS - Akamai Technologies, Inc., US | |||
| 1,039,393,739 | 2.25% | AS6453 | TATA COMMUNICATIONS (AMERICA) INC, US | |||
| 656,791,255 | 1.42% | AS15133 | EDGECAST - MCI Communications Services, Inc. d/b/a Verizon Business, US | |||
| 596,751,215 | 1.29% | AS33438 | HIGHWINDS2 - Highwinds Network Group, Inc., US | |||
| 469,360,413 | 1.02% | AS50952 | DATAIX-AS Peering Ltd., RU | |||
| 1,933,668,193 | 4.19% | other |
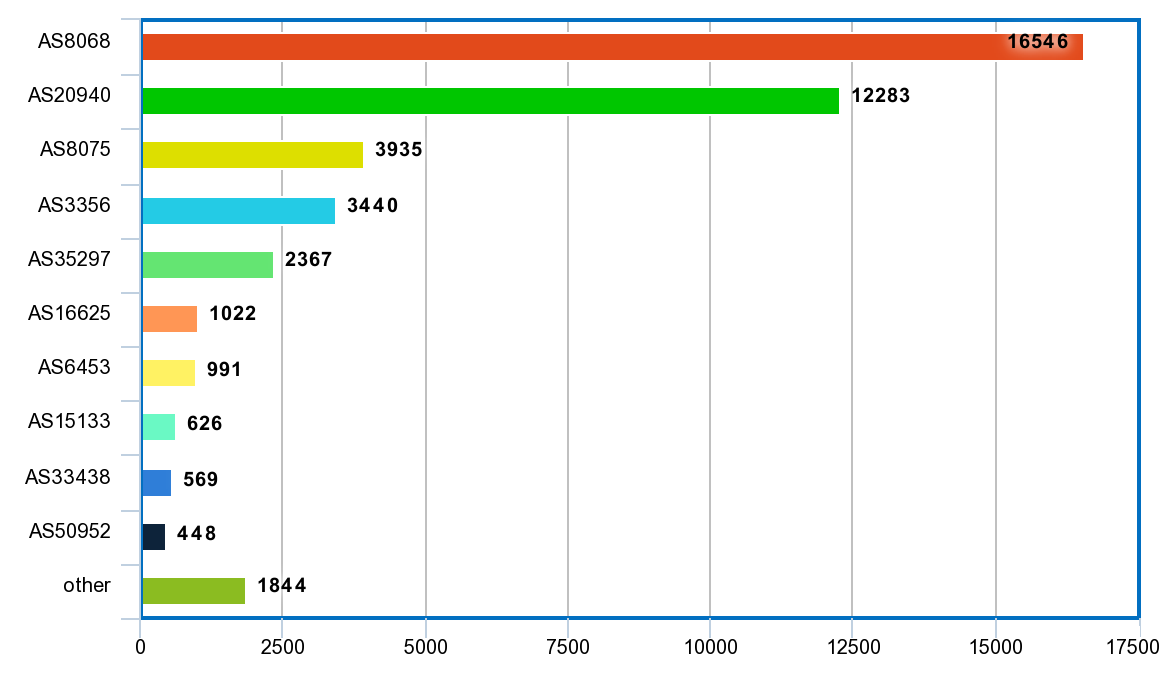
Conclusion: two Microsoft autonomous systems clearly dominate, but there are others as well. Autonomous systems of AKAMAI, LEVEL3 and other cloud providers can’t be blocked on the firewall level, because normal operation of too many systems will be broken — stable connectivity to these servers is required not only by Microsoft’s products.
What is being collected and transferred
Let’s look into Microsoft Privacy Statement. It has over 50 pages, so here will be a partial quote:
Your privacy is important to us.
[…]
The data we collect can include the following:
Name and contact data. We collect your first and last name, email address, postal address, phone number, and other similar contact data.
Credentials. We collect passwords, password hints, and similar security information used for authentication and account access.
Demographic data. We collect data about you such as your age, gender, country, and preferred language.
Payment data. We collect data necessary to process your payment if you make purchases, such as your payment instrument number (such as a credit card number), and the security code associated with your payment instrument.
Device and Usage data. We collect data about your device and how you and your device interact with Microsoft and our products. For example, we collect:
- Product use data. We collect data about the features you use, the items you purchase, and the web pages you visit. This data includes your voice and text search queries or commands to Bing, Cortana, and our chat bots. This also includes the settings you select and the software configurations your use most.
- Device, connectivity and configuration data. We collect data about your device and the network you use to connect to our products. It includes data about the operating systems and other software installed on your device, including product keys. It also includes IP address, device identifiers (such as the IMEI number for phones), regional and language settings.
- Error reports and performance data. We collect data about the performance of the products and any problems you experience with them. This data helps us to diagnose problems in the products you use, and to improve our products and provide solutions. Depending on your product and settings, error reports (sometimes called “crash dumps”) can include data such as the type or severity of the problem, details of the software or hardware related to an error, contents of files you were using when an error occurred, and data about other software on your device.
- Troubleshooting and Help Data. When you engage Microsoft for troubleshooting and help, we collect data about you and your hardware, software, and other details related to the incident. Such data includes contact or authentication data, the content of your chats and other communications with Microsoft, data about the condition of the machine and the application when the fault occurred and during diagnostics, and system and registry data about software installations and hardware configurations.
Interests and favorites. We collect data about your interests and favorites, such as the teams you follow in a sports app, the programming languages you prefer, the stocks you track in a finance app, or the favorite cities you add to a weather app. In addition to those you explicitly provide, your interests and favorites may also be inferred or derived from other data we collect.
Contacts and relationships. We collect data about your contacts and relationships if you use a Microsoft product to manage contacts, for example Outlook.com, or to communicate or interact with other people or organizations, for example Visual Studio Team Services.
Location data. For products with location-enhanced features, we collect data about your location, which can be either precise or imprecise. Precise location data can be Global Navigation Satellite System (GNSS) data (e.g., GPS), as well as data identifying nearby cell towers and Wi-Fi hotspots, we collect when you enable location-based products or features. Imprecise location data includes, for example, a location derived from your IP address or data that indicates where you are located with less precision, such as at a city or postal code level.
Content. We collect content of your files and communications when necessary to provide you with the products you use. For example, if you transmit a file using Skype to another Skype user, we need to collect the content of that file to display it to you and the other user as you direct. If you receive an email using Outlook.com, we need to collect the content of that email to deliver it to your inbox, display it to you, enable you to reply to it, and store it for you until you choose to delete it. Other data we collect to provide communication services to you include the:
- subject line and body of an email,
- text or other content of an instant message,
- audio and video recording of a video message, and
- audio recording and transcript of a voice message you receive or a text message you dictate.
[…]
We also obtain data from third parties. We protect data obtained from third parties according to the practices described in this statement, plus any additional restrictions imposed by the source of the data. These third-party sources vary over time, but have included:
- Data brokers from which we purchase demographic data to supplement the data we collect. Social networks when you grant permission to a Microsoft product to access your data on one or more networks.
- Service providers that help us determine a location based on your IP address in order to customize certain products to your location.
- Partners with which we offer co-branded services or engage in joint marketing activities, and
- Publicly-available sources such as open government databases or other data in the public domain.
So, essentially:
They collect your first and last name, email address, postal address, phone number, and other similar contact data
They collect data about you such as your age, gender, country, location
They collect data about your interests
They collect data about your contacts and relationships
They collect passwords
They collect security code associated with your payment instrument
They collect data about other software installed on your device
They collect content of your files and communications
And if they have collected not enough data, they get it from third parties